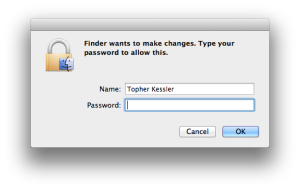
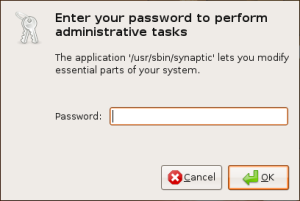
Hello, old blog friend.
Sorry for neglecting you lately. I don’t allocate as much time to OS research these days as the subject would warrant. I currently prefer to prioritize things like my precarious academic job and hobbies that fit better into the small time slices that I manage to allocate away from it, such as learning Rust and trying to build better Linux performance analysis tools with it.
I know it’s not an excuse, and I would like to get back to OS work at some point. Especially as every day remains a reminder of all that’s wrong about today’s operating systems and the abstractions that they present. And so today, I would like to discuss one particular OS abstraction that IMHO has not aged well and would be in need of a serious redesign in the next generation of operating systems: threads.